
Top Tools for SSL/TLS Debugging on macOS
Debugging SSL/TLS issues on macOS can be tricky, but the right tools make it easier. Whether you're troubleshooting certificate errors, handshake failures, or protocol mismatches, this guide covers the best command-line and GUI tools to simplify the process. Here's a quick overview:
-
Command-Line Tools:
- OpenSSL: Analyze handshakes, certificates, and protocols.
- tcpdump: Capture and inspect raw network packets.
- nscurl: Test App Transport Security (ATS) compliance for macOS/iOS apps.
-
GUI Applications:
- ReqRes: Real-time HTTP(S) traffic debugging with features like local mapping and endpoint simulation.
- Proxyman: Visualize SSL/TLS details like certificates and ciphers.
- Charles Proxy: Advanced testing with breakpoints, throttling, and rewrite rules.
-
Security Testing:
- SSLScan: Check server configurations for insecure protocols or ciphers.
- testssl.sh: Identify vulnerabilities like Heartbleed or POODLE.
Quick Comparison:
| Tool | Purpose | Best For |
|---|---|---|
| OpenSSL | Handshake, certificate analysis | General debugging, protocol-specific tests |
| tcpdump | Packet-level traffic inspection | Low-level network analysis |
| nscurl | ATS compliance testing | macOS/iOS app development |
| ReqRes | Real-time HTTP(S) debugging | Simplifying SSL/TLS tests |
| Proxyman | SSL/TLS visualization | User-friendly debugging, mobile apps |
| Charles Proxy | Advanced testing, traffic control | Complex debugging, edge case simulations |
| SSLScan | Server configuration checks | Compliance and security checks |
| testssl.sh | Vulnerability testing | Identifying protocol weaknesses |
Key Tips:
- Start with tools like OpenSSL to diagnose issues quickly.
- Use GUI apps for visual debugging and team collaboration.
- Regularly test your server's security with tools like SSLScan and testssl.sh.
- Address macOS-specific quirks, such as keychain certificate validation, to avoid hidden issues.
This article dives deeper into how each tool works and provides step-by-step guidance for effective SSL/TLS debugging on macOS.
Command-Line Tools for SSL/TLS Debugging
When SSL/TLS issues arise, command-line tools can be a quick and effective way to get to the root of the problem. These tools give you direct access to protocol-level details, often uncovering issues that graphical interfaces might miss. macOS comes with some built-in options, but you can also expand your toolkit by installing additional utilities.
OpenSSL for Testing Handshakes

OpenSSL is a go-to tool for SSL/TLS debugging, particularly useful for macOS. According to the OpenSSL documentation:
"This command implements a generic SSL/TLS client which connects to a remote host using SSL/TLS. It is a very useful diagnostic tool for SSL servers."
The s_client command is a standout feature, providing insights into client-server interactions. It can check if a port is open, confirm secure connections, display the SSL certificate in use, and even reveal when that certificate expires. For example, to test a connection, you can run:
openssl s_client -connect example.com:443
This command will show the certificate chain, handshake details, and cipher information. For a more concise output, use the -brief flag. If you're working in a non-interactive environment, the -ign_eof flag prevents the connection from closing prematurely.
To check certificate details like expiration dates or Subject Alternative Names (SANs), you can pipe the output of s_client to x509:
echo | openssl s_client -connect example.org:443 2>/dev/null | openssl x509 -noout -dates
If you need to test specific protocol versions (handy for legacy systems or strict security setups), you can specify them with flags like -tls1_1, -tls1_2, or -tls1_3.
In January 2021, Google showcased the utility of OpenSSL by testing TLS connectivity to www.google.com on port 443. The following command:
openssl s_client -connect www.google.com:443
successfully verified a TLSv1.2 connection using the ECDHE-RSA-CHACHA20-POLY1305 cipher. It also displayed the complete certificate chain and handshake details.
While OpenSSL is excellent for handshake and certificate analysis, you might need tcpdump for deeper packet-level insights.
Capturing Traffic with tcpdump
Once you've examined handshake details with OpenSSL, tcpdump can help you dig into the raw network packets behind SSL/TLS communication. This tool focuses on capturing the data that moves across the network, offering a different perspective than application-layer analysis. Since SSL/TLS handshakes typically occur on port 443 (used for HTTPS), you can filter traffic with a simple command:
tcpdump -i en0 port 443
This captures all HTTPS traffic on your primary network interface. If you want to narrow it down to a specific host, use:
tcpdump -i en0 host example.com and port 443
For further analysis, you can save the captured packets using the -w flag:
tcpdump -i en0 port 443 -w ssl_debug.pcap
The saved file can be reviewed later with tools like Wireshark. Additionally, examining timing information in the output can help identify network delays that might cause SSL/TLS timeouts.
macOS-Specific Tools like nscurl
macOS developers often face unique challenges due to App Transport Security (ATS), Apple's framework for enforcing secure connections. The nscurl tool is specifically designed to test ATS configurations and ensure compatibility with macOS's security requirements.
To check your server's ATS compliance, you can run:
nscurl --ats-diagnostics --verbose https://yourdomain.com
This diagnostic mode performs multiple tests under various ATS settings, clearly indicating which configurations succeed or fail. For developers working on iOS or macOS apps, confirming ATS compatibility is a critical step before launching in production. If needed, you can also use the full path:
/usr/bin/nscurl --ats-diagnostics --verbose https://yourdomain.com
This ensures a thorough check of your server's configuration.
| Tool | Primary Use Cases | Best For |
|---|---|---|
| OpenSSL s_client | Certificate validation, handshake testing, protocol verification | General SSL/TLS debugging, cross-platform issues |
| tcpdump | Packet-level analysis, timing issues, network problems | Low-level debugging, performance analysis |
| nscurl | ATS compliance, macOS-specific SSL requirements | iOS/macOS app development, Apple ecosystem |
GUI Applications for SSL/TLS Debugging on macOS
Command-line tools are undeniably powerful for SSL/TLS debugging, but sometimes you need a more visual and intuitive approach. That’s where GUI applications come in. These tools make troubleshooting SSL/TLS issues easier with point-and-click interfaces, making them accessible to a broader range of users, including those who might not be as comfortable with command-line methods. Plus, they’re great for team collaboration, especially when you’re working with people from different technical backgrounds.
ReqRes: Native macOS HTTP(S) Debugging
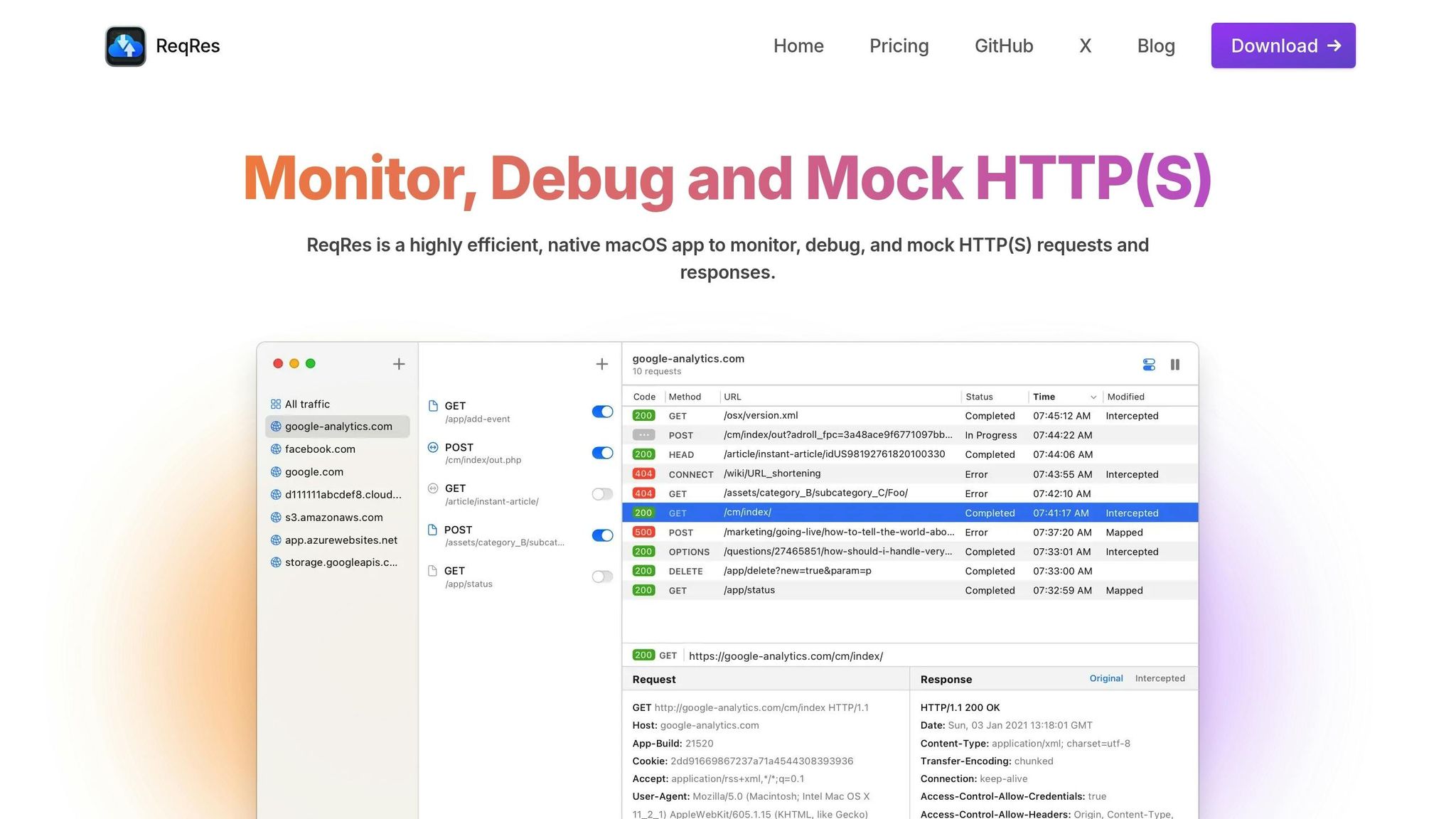
ReqRes is a native macOS application designed to simplify SSL/TLS debugging. It captures HTTP(S) traffic in real time, allowing you to see requests and responses as they happen. This live visibility makes it much easier to diagnose handshake or certificate timing issues. Whether you’re testing browsers or native apps, ReqRes lets you monitor how they handle SSL/TLS connections.
One standout feature is the Map Local Tool, which lets you use local files as responses. This means you can simulate various certificate scenarios - like expired certificates or alternative certificate chains - without needing to tweak server configurations. It’s a quick way to test how your application reacts to different SSL/TLS setups.
ReqRes also excels at creating controlled testing environments with its advanced mocking capabilities. You can simulate entire endpoints, making it possible to reproduce edge cases like certificate validation failures or specific cipher suite negotiations. These scenarios can be tricky to replicate with live servers, but ReqRes makes it straightforward.
Another highlight is its one-click setup for traffic inspection. Unlike other tools that require complex proxy configurations, ReqRes gets you up and running quickly, so you can dive into debugging without wasting time on setup.
Here’s a quick look at ReqRes pricing:
| Plan | Price | Devices | Key Benefits |
|---|---|---|---|
| Single Device | $59.99 | 1 | All premium features, 1-year updates |
| Two Devices | $69.99 | 2 | 30% discount, great for developers with multiple Macs |
| Team Plan | $149.99 | Up to 5 | Best value for development teams |
Proxyman for SSL/TLS Analysis
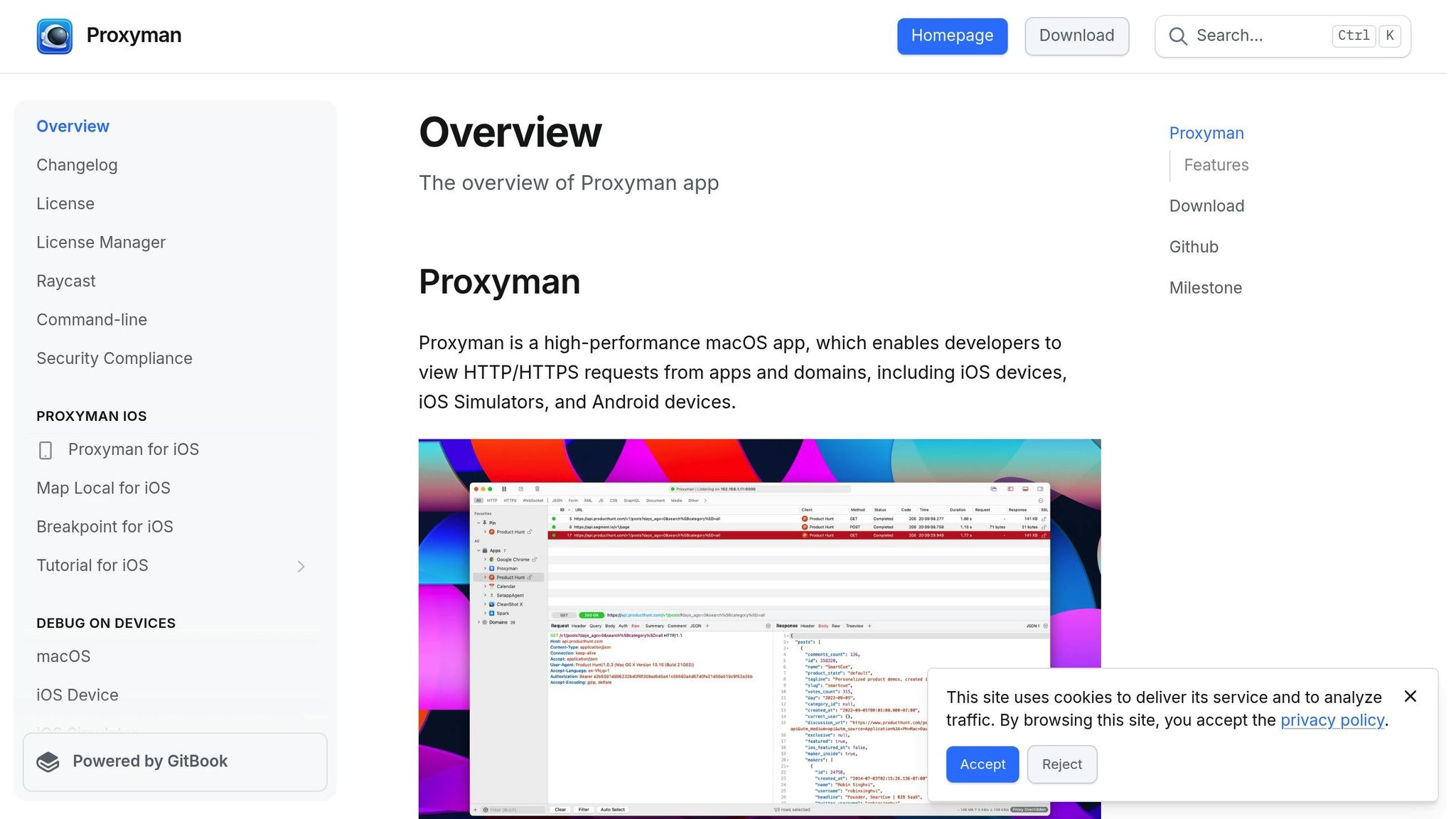
Proxyman is another macOS-focused tool that excels at capturing HTTP/HTTPS requests, making it particularly useful for mobile app developers dealing with SSL/TLS issues. It’s equipped with features like WebSocket and TLS 1.3 inspection, which are essential for modern debugging tasks.
What sets Proxyman apart is its user-friendly interface, which visually breaks down SSL/TLS details like certificate chains, cipher negotiations, and protocol versions. This clear presentation makes it easier to spot issues such as weak cipher suites or certificate validation errors. It’s a practical choice for developers who want to quickly identify and address SSL/TLS problems.
Charles Proxy for Complex Testing

Charles Proxy is a go-to tool for more advanced SSL/TLS debugging needs. As described by its creators:
"Charles is an HTTP proxy / HTTP monitor / Reverse Proxy that enables a developer to view all of the HTTP and SSL / HTTPS traffic between their machine and the Internet."
One of its standout features is breakpoint control. With breakpoints, you can pause and edit API requests and responses or even decide whether to block or allow them. This is especially useful for testing how applications handle SSL/TLS errors or for tweaking certificate-related headers during debugging.
Charles Proxy also includes bandwidth throttling, which lets you simulate slower network conditions. This is invaluable when you need to test how SSL/TLS handshakes behave under less-than-ideal circumstances, such as timeouts or partial handshake failures.
Another powerful feature is its rewrite rules, which allow you to modify SSL/TLS headers and responses on the fly. This capability is crucial for testing how applications handle different certificate authorities, certificate types, or security headers like HSTS (HTTP Strict Transport Security).
Charles Proxy offers a free trial, so you can explore its features before committing to a paid license.
These GUI tools are excellent complements to command-line options like OpenSSL and tcpdump. While the latter are great for in-depth, low-level analysis, GUI applications shine when you need to quickly test scenarios, visualize SSL/TLS details, or collaborate with team members who prefer a point-and-click approach. Together, they provide a well-rounded toolkit for tackling SSL/TLS debugging on macOS.
Security Testing Tools for SSL/TLS
Once you've tackled visual debugging, the next step is ensuring your server's security is up to par. This is where specialized tools come in handy, as they can uncover vulnerabilities and configuration issues that basic debugging might overlook. These tools are essential for a complete SSL/TLS security toolkit.
SSLScan for Configuration Insights

SSLScan is a command-line utility designed to give you a thorough snapshot of your server's SSL/TLS security setup. It uses a simple yet effective color-coding system: red flags insecure configurations, while green and white indicate secure ones. By connecting to your server, SSLScan delivers a detailed list of all the protocols and ciphers your server supports.
This tool is particularly useful for compliance checks. It ensures your SSL/TLS settings align with industry standards like CIS, HIPAA, or GDPR. The latest version, SSLScan 2, brings significant upgrades. Its scanning capabilities have been completely revamped, eliminating reliance on your local OpenSSL version for many checks. Additionally, it supports XML output, making it easier to integrate results with other security tools.
For a broader protocol assessment, testssl.sh offers a complementary solution.
testssl.sh for Protocol Vulnerability Testing
testssl.sh is a free, open-source tool that evaluates SSL/TLS configurations on any port. It tests for supported ciphers, protocols, and common cryptographic vulnerabilities. One of its standout features is its ability to test 370 preconfigured ciphers.
This tool is highly effective at identifying critical vulnerabilities like POODLE, Heartbleed, DROWN, ROBOT, and Ticketbleed. It’s versatile enough to assess any SSL/TLS-enabled service and even supports STARTTLS for protocols such as FTP, SMTP, POP3, and IMAP, making it adaptable to a variety of infrastructures.
Privacy is another strength of testssl.sh. Since it runs locally, your test results remain entirely under your control. It also supports multiple output formats, including colorful terminal displays, JSON, and CSV. For larger-scale testing, it can handle mass assessments in both serial and parallel modes. To simplify repetitive tasks, you can preset command-line options using environment variables.
Both SSLScan and testssl.sh not only identify vulnerabilities but also provide detailed recommendations for fixing them, giving you clear steps to strengthen your server's security.
SSL/TLS Debugging Best Practices on macOS
Debugging SSL/TLS issues can feel like navigating a maze, but having a clear plan and the right tools makes all the difference. With studies showing that 90% of applications tested have some form of misconfiguration, a structured approach can save you time and ensure security vulnerabilities don’t slip into production.
Step-by-Step Debugging Process
Start by gathering error messages and cross-referencing them with known fixes to identify whether the issue stems from the client, server, or an intermediary. Begin with command-line tools like OpenSSL for diagnostics. If the problem persists, use GUI tools such as ReqRes, which can capture and display HTTP(S) traffic in real time. This helps you identify certificate chain issues or handshake failures that might not be evident in terminal outputs.
Next, isolate your application to determine if the root cause lies in your code or the SSL/TLS configuration. This systematic approach links initial troubleshooting with deeper performance and security assessments.
Performance and Security Tips
Once you’ve addressed the initial issues, enable detailed logging to capture the complete handshake process. This includes critical steps like cipher selection and certificate validation, which can reveal hidden problems.
Stick to the latest TLS versions and secure ciphers to avoid compatibility issues and potential vulnerabilities. Older protocols often cause connection errors with modern servers that have phased out legacy support.
Incorporate SSL/TLS checks into your development workflow. Regularly monitor certificate expiration dates, cipher strength, and protocol support. This proactive step ensures you catch issues early, long before deployment.
Fixing macOS-Specific Problems
macOS introduces its own quirks, which require precise solutions rather than quick fixes. For instance, macOS often validates certificates against the system keystore, even if they’re missing from OpenSSL’s keystore. This can obscure underlying problems.
Avoid insecure shortcuts and address certificate issues properly by replacing faulty certificates or implementing certificate/public key pinning. If peer configurations seem to work, analyze their traffic to adjust your protocol version and ciphers without compromising security. Addressing these macOS-specific challenges head-on ensures a more reliable and secure SSL/TLS configuration.
Conclusion
Debugging SSL/TLS issues on macOS is a crucial skill for maintaining secure and reliable systems. As highlighted earlier, misconfigurations are a frequent challenge, making it essential to have a robust set of tools at your disposal.
The key is to select tools that align with each phase of the debugging process. Command-line utilities like OpenSSL and tcpdump provide detailed diagnostics, while GUI tools such as ReqRes offer a more user-friendly way to monitor and debug HTTP(S) traffic in real time. For pinpointing vulnerabilities, tools like SSLScan and testssl.sh are indispensable, helping you address potential issues before they become critical.
Effective SSL/TLS debugging involves a structured approach. Begin by analyzing error messages and using the right tools to pinpoint the source of the problem - whether it’s the client, server, or an intermediary. Avoid quick fixes that might compromise security; instead, focus on resolving the core issue.
To stay ahead of potential problems, integrate SSL/TLS validation into your CI/CD pipelines and set up monitoring tools with real-time alerts. This proactive strategy is especially important for tackling macOS-specific quirks, such as keystore validation issues and unique behaviors in Secure Transport.
This guide emphasizes the balance between powerful command-line utilities and intuitive GUI applications like ReqRes. macOS presents its own set of challenges, but with the outlined tools and techniques, you’ll be well-equipped to handle certificate chain issues, handshake failures, and other SSL/TLS hurdles - all while maintaining top-tier security practices.
FAQs
What makes GUI tools like ReqRes better than command-line tools for SSL/TLS debugging on macOS?
GUI tools like ReqRes bring a lot to the table when it comes to SSL/TLS debugging on macOS. Unlike command-line tools, they provide a clean, visual interface that simplifies the process of analyzing SSL/TLS traffic. You don’t have to wrestle with remembering cryptic commands - everything is laid out in an intuitive way, making it especially handy for developers who prefer a graphical workflow or aren’t as comfortable with terminal commands.
On top of that, GUI tools often come packed with extra features like real-time traffic monitoring, endpoint mocking, and easy-to-navigate configuration settings. These features can help you work faster and more efficiently. By giving you a clear, interactive view of SSL/TLS activity, tools like these make debugging less of a headache and more approachable for developers, whether you're just starting out or have years of experience.
What tools can I use on macOS to ensure my server's SSL/TLS setup meets industry standards?
To keep your server's SSL/TLS configuration aligned with industry standards, macOS provides some effective tools. SSLyze is a handy option for scanning your server, identifying vulnerabilities, and checking if it meets best practices. Meanwhile, testssl.sh offers in-depth analysis, looking at supported ciphers, protocols, and any potential misconfigurations.
Another useful tool is ReqRes, which allows real-time monitoring and debugging of HTTP(S) traffic. This makes it easier to spot and fix SSL/TLS issues during development or testing. With these tools in your toolkit, you can thoroughly assess and fine-tune your server's security setup.
What challenges do macOS users face when debugging SSL/TLS issues, and how can they resolve them?
Debugging SSL/TLS on macOS can feel daunting, thanks to the complexity of the protocol and the often cryptic error messages that come with it. Issues like handshake failures are common, often stemming from misconfigured SSL stacks or applications that don’t handle these errors well.
Thankfully, tools like OpenSSL can make the process much more manageable. For instance, running the openssl s_client command allows you to test SSL/TLS connections and uncover handshake problems. Another helpful approach is enabling CFNetwork diagnostic logging on macOS. This provides detailed logs of network activity, offering valuable insights to pinpoint issues.
By combining these tools and techniques, developers can more effectively troubleshoot and resolve SSL/TLS problems on macOS.