
What is Mitmproxy?
Mitmproxy is a free, open-source HTTPS proxy tool that lets you intercept, inspect, and modify web traffic in real time. It's widely used by developers, testers, and security professionals to debug, analyze, and test network traffic. Here's what you need to know:
-
Key Features:
- Intercepts HTTP/1, HTTP/2, HTTP/3, WebSockets, and encrypted SSL/TLS traffic.
- Decrypts HTTPS traffic using dynamic certificate creation.
- Offers three interfaces: a terminal-based console (
mitmproxy), a web interface (mitmweb), and a command-line tool for automation (mitmdump). - Allows modification of requests and responses to simulate different scenarios.
- Supports filtering traffic by domains, status codes, and more.
-
Why Use It?
- Debug APIs and web applications by inspecting requests and responses.
- Test mobile apps by monitoring their network traffic.
- Perform penetration testing to identify vulnerabilities and ensure data security.
-
Installation on macOS:
- Use Homebrew:
brew install mitmproxy. - Configure proxy settings and trust Mitmproxy's Certificate Authority (CA) to decrypt HTTPS traffic.
- Use Homebrew:
Mitmproxy is a versatile tool for analyzing and debugging network traffic, whether you're working on APIs, web apps, or mobile applications. It's free, open-source, and highly customizable with a Python API for advanced use cases.
Core Features of Mitmproxy
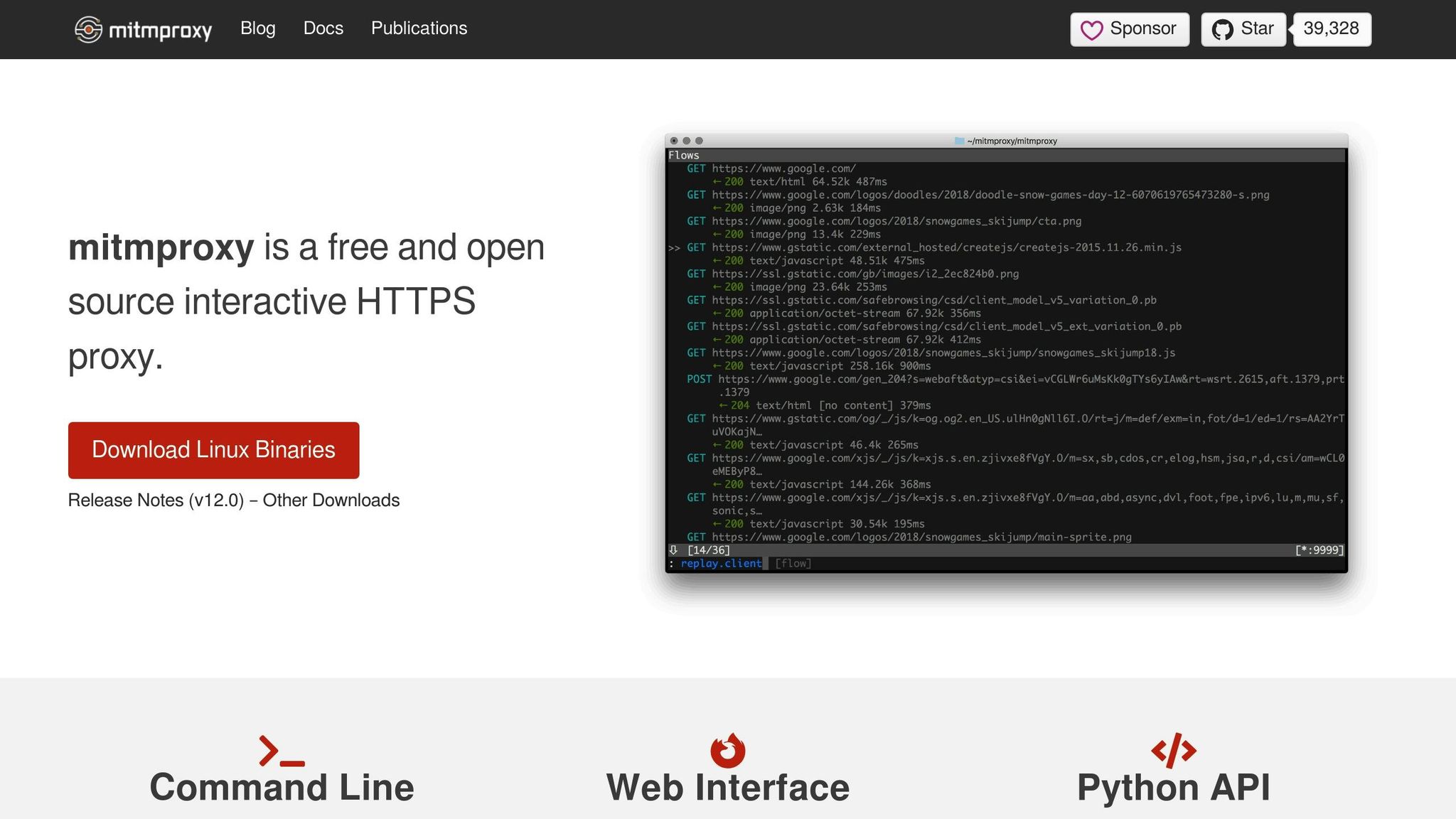
Traffic Interception and Inspection
At the heart of Mitmproxy's functionality is its ability to intercept and inspect network traffic - a feature that makes debugging seamless. It supports a wide range of protocols, including HTTP/1, HTTP/2, HTTP/3, WebSockets, and SSL/TLS-encrypted traffic, all in real time. This broad compatibility ensures you can debug modern web applications no matter which HTTP version they use.
One standout feature is dynamic certificate generation, which decrypts HTTPS traffic on-the-fly. This means you gain transparent access to encrypted data without disrupting the normal operation of your applications. You can monitor their network behavior with ease while everything continues to run smoothly.
Mitmproxy also simplifies the debugging process by formatting messages for readability. Whether you're dealing with HTML, Protobuf, or other message types, the tool presents clean, formatted output instead of raw binary data or compressed responses. This clarity makes it much easier to understand your network interactions.
Another invaluable feature is the ability to save complete HTTP conversations for later analysis. By capturing problematic interactions, you can replay them to reproduce bugs and test fixes without relying on live traffic. This capability is a game-changer for troubleshooting complex issues.
These powerful interception tools lay the foundation for Mitmproxy's flexible interface options.
Interface Options
Mitmproxy caters to different workflows with three distinct interfaces, each designed to suit specific user preferences. The interactive console (mitmproxy) provides a terminal-based experience with convenient keyboard shortcuts. For those who prefer a graphical approach, the web interface (mitmweb) offers a user-friendly interface similar to Chrome DevTools. Lastly, Mitmdump is perfect for command-line automation, making it ideal for batch processing and testing tasks.
All three interfaces run on the same robust engine, allowing you to switch between them effortlessly depending on your needs.
In addition to these interfaces, Mitmproxy offers advanced filtering and modification tools to refine your debugging process.
Filtering and Modification Tools
Mitmproxy's filtering tools make it easy to isolate traffic based on criteria like domain, status codes, or custom parameters. Meanwhile, its real-time modification features - such as anticache, map_local, map_remote, and header/body editing - let you test various network conditions with precision.
Some of these tools stand out for their specialized functionality. The anticache feature ensures you capture complete HTTP exchanges by bypassing cached responses. The map_local option redirects requests to local files, allowing you to test modified content without changing server-side files. Similarly, the map_remote option replaces URLs before requests reach the server, enabling flexible testing scenarios.
For more granular control, body and header modification tools are invaluable. The modify_body feature lets you edit request and response content in real time, while modify_headers allows you to adjust headers with pinpoint accuracy. These tools make it easier to simulate challenging network conditions and replicate edge cases that are hard to encounter naturally.
To take things even further, Mitmproxy integrates with a Python API. This allows you to create custom scripts and addons to automate complex debugging tasks. Whether you need to analyze traffic in-depth or simulate unique scenarios, this programmable option gives you the flexibility to tailor the tool to your exact requirements.
Installing Mitmproxy on macOS
Mitmproxy is a powerful tool for debugging network traffic, and setting it up on macOS is a straightforward process. To get started, you'll need to install the software, configure your network settings, and set up certificate trust. Once installed, Mitmproxy can intercept and debug traffic effectively.
Installation Using Homebrew

Homebrew, a popular package manager for macOS, is the easiest way to install Mitmproxy. It simplifies the installation process and manages dependencies seamlessly. Before you proceed, make sure your Mac is running macOS 10.11 or later, which is required for Mitmproxy version 12.1.1.
If Homebrew isn't already installed on your system, you'll need to install it first. Once that's done, you can install Mitmproxy with a single command:
brew install --cask mitmproxy
This command installs all three Mitmproxy interfaces: the interactive console, the web interface, and the command-line tool. To verify the installation, run the following commands:
mitmproxy # Launches the interactive console
mitmweb # Opens the web-based interface
mitmdump # Runs the command-line interface
Each command should open its respective interface. To exit, use Ctrl+C or type the quit command.
Configuring macOS Network Settings
Mitmproxy offers several methods to capture traffic, with local redirect mode being the preferred option for macOS. However, understanding traditional proxy configuration can be useful for specific testing scenarios.
To set up a system-wide proxy:
- Open System Preferences > Network > Wi-Fi, then click Advanced > Proxies.
- Enable both Web Proxy (HTTP) and Secure Web Proxy (HTTPS).
- Enter
127.0.0.1as the server address and8080as the port.
This configuration routes all HTTP and HTTPS traffic through Mitmproxy's default port.
If you need to intercept traffic from a mobile device, find your Mac's IP address under System Preferences > Network. Then, configure the device's manual proxy settings to use your Mac's IP and port 8080.
For macOS applications, local redirect mode is especially helpful because it captures traffic without requiring manual proxy adjustments for individual apps.
Installing and Trusting CA Certificates
To decrypt HTTPS traffic, Mitmproxy relies on its own Certificate Authority (CA). This certificate must be trusted by your system to function properly. When you first run Mitmproxy, it generates a unique CA certificate.
The easiest way to install the certificate is through Mitmproxy's built-in certificate app. Start any Mitmproxy interface, set up your device to use it as a proxy, and visit mitm.it in a browser. The site will automatically detect your device and provide the correct certificate format along with step-by-step installation instructions.
For manual installation on macOS, use the following command:
sudo security add-trusted-cert -d -p ssl -p basic -k /Library/Keychains/System.keychain ~/.mitmproxy/mitmproxy-ca-cert.pem
This command adds the certificate to your system keychain with the proper trust settings. After completing this step, restart your browser to apply the changes.
Note for iOS users: If you're intercepting traffic from an iPhone or iPad, installing the certificate alone isn't enough. You'll also need to enable full trust for the certificate. Go to Settings > General > About > Certificate Trust Settings and toggle on the Mitmproxy certificate. This additional step is required for recent iOS versions.
Once everything is configured, Mitmproxy is ready to capture and analyze your network traffic with ease.
Common Use Cases for Mitmproxy
Mitmproxy simplifies debugging tasks for developers and testers, making it a go-to tool for scenarios like API debugging, mobile app testing, and network analysis. Its core features provide practical solutions for uncovering and resolving network-related issues.
Inspecting HTTP Requests
One of Mitmproxy's standout abilities is capturing and analyzing HTTP requests and responses. By configuring your browser to route traffic through Mitmproxy, you gain a detailed view of every HTTP request, including headers, content, and metadata. This level of visibility helps uncover issues that might not show up in your application's logs.
When debugging APIs, Mitmproxy shines by identifying slow responses or oversized payloads. It makes spotting sluggish endpoints or unexpectedly large data transfers straightforward. With filtering options, you can zero in on specific hostnames or request types, cutting through unnecessary noise. By examining intercepted traffic, you can confirm the accuracy of the data being sent and received - ideal for catching problems like malformed JSON or missing parameters. Beyond just monitoring, Mitmproxy allows you to simulate server responses, enabling you to test your application’s error handling under various conditions. This makes it an invaluable tool for uncovering subtle network issues.
Modifying API Requests and Responses
Mitmproxy is a powerful tool for intercepting and modifying HTTP/HTTPS requests and responses, making it perfect for testing scenarios that are otherwise difficult to replicate. Using the intercept command, you can pause requests before they reach the server, allowing you to tweak headers, modify request bodies, or even redirect requests entirely.
For more advanced needs, Mitmproxy supports custom addons that listen to network events and provide programmatic control over traffic. With these, developers can simulate complex conditions, such as triggering specific API states or introducing errors. This flexibility makes Mitmproxy a versatile option for creating intricate testing setups tailored to unique requirements.
Monitoring Mobile App Traffic
Mitmproxy is equally effective for debugging mobile applications. To monitor mobile app traffic, ensure your computer running Mitmproxy and your mobile device are on the same Wi-Fi network. Then, configure the mobile device to use your computer as a proxy server, ensuring all network traffic flows through Mitmproxy for inspection.
For Android devices, this typically involves adjusting Wi-Fi settings to include your computer's IP address and port 8080 as proxy settings. The Mitmweb interface, accessible at 127.0.0.1:8081 on your computer, provides an easy way to view and analyze intercepted traffic from your mobile device.
One challenge to keep in mind is certificate pinning. If an app uses certificate pinning, you’ll need to adjust its network security settings to allow custom CA certificates. Monitoring mobile traffic not only helps debug app behavior but also ensures sensitive information like authentication tokens or personal data isn’t unintentionally exposed.
Best Practices and Security Tips
Using Mitmproxy effectively means balancing its powerful debugging capabilities with strict security measures and adherence to legal requirements. Following best practices ensures your data remains secure while maximizing the tool's usefulness in professional settings.
Ethical Use and Compliance
Before using Mitmproxy, always obtain explicit permission, especially when working on systems you don’t own. This includes corporate networks, shared Wi-Fi, and devices belonging to others. Intercepting traffic without authorization could violate privacy laws, so it's essential to stay within legal boundaries.
In enterprise environments, align your testing activities with your organization's security policies and data governance rules. Clearly define the scope of your testing - specifying the systems, duration, and data access involved. This is particularly critical when testing mobile apps that may handle user data or integrate with third-party APIs.
Keep detailed logs during security assessments to document authorized testing activities. These logs can help differentiate your work from malicious actions, providing a clear record of compliance.
Once you’ve secured authorization, prioritize safeguarding sensitive data throughout your testing sessions.
Handling Sensitive Data
Network traffic often includes sensitive information like personal details, login credentials, financial records, or confidential business data, making data protection a top priority.
- CA Certificates: Install Mitmproxy’s CA certificate only on trusted devices. Remove it immediately after testing to prevent unauthorized access to encrypted traffic.
- Filtered Traffic: Use Mitmproxy’s filtering tools to capture only the traffic relevant to your debugging tasks. For instance, if you’re testing a specific API endpoint, focus on that domain rather than intercepting all network activity.
- Sensitive Data: Avoid logging or storing authentication tokens, session cookies, or other sensitive values in plain text. If analyzing authentication flows, concentrate on the structure and timing of requests rather than the actual credentials. Mitmproxy’s scripting tools can help redact sensitive fields automatically.
- Data Retention: Implement policies that limit how long captured traffic is stored and restrict access to it. Analyze data promptly, then delete it securely to minimize risk.
By addressing ethical considerations and protecting sensitive information, you can use Mitmproxy responsibly. Next, let’s look at how to optimize its performance for handling large traffic volumes.
Performance Tips
When dealing with high traffic volumes, Mitmproxy can experience slowdowns. Applying strategic filtering and configuration tweaks can help you maintain performance without sacrificing debugging precision.
- Host Filtering: Focus on traffic from relevant domains. For example, exclude unnecessary traffic with commands like
mitmproxy --ignore-hosts '.*google\.com'. This reduces resource usage and improves efficiency. - Mitmdump for Automation: Use
mitmdumpfor scripting and handling large datasets. Its command-line interface is more resource-efficient than interactive modes, making it ideal for extended or automated testing. - Adjust Detail Levels: Reduce output verbosity in
mitmdumpto optimize performance. Limiting content view lines and storing streamed bodies only when necessary can significantly lower memory usage during long sessions. - Monitor Resources: Keep an eye on system resources, particularly RAM, during extended testing. Use log rotation and external storage for long-term analysis instead of relying solely on memory.
- Configuration Tweaks: Tailor your
~/.mitmproxy/config.yamlfile to match your typical workflows. Adjust settings like connection timeouts, maximum concurrent connections, and content filtering rules to strike the right balance between performance and debugging efficiency.
Finally, make sure you’re always running the latest version of Mitmproxy to benefit from performance updates and security fixes. These small adjustments can make a big difference when handling demanding debugging tasks.
Conclusion
Mitmproxy proves to be a powerful ally for developers and testers on macOS, offering deep insights into HTTP(S) traffic. Its robust features and ease of use make it a go-to tool for tasks like API debugging, mobile app testing, and network troubleshooting. This article has explored how Mitmproxy simplifies these processes on macOS.
Key Takeaways
Mitmproxy's three interface options - command-line, web-based, and scripting - offer flexibility to suit different workflows. Whether you need quick command-line efficiency, a user-friendly web interface, or the ability to automate tasks, Mitmproxy has you covered. Its real-time traffic interception reveals how applications interact with APIs and external services, ensuring you stay informed about data flows.
The tool also enables active testing by letting you modify requests, simulate responses, and test edge cases. These features are particularly helpful for penetration testing and identifying vulnerabilities.
With over 39,000 stars on GitHub, Mitmproxy has earned a strong reputation among developers worldwide. Its open-source nature ensures top-tier functionality without the constraints of licensing fees or vendor lock-in, making it an accessible choice for teams of all sizes.
The Python API integration takes things a step further by allowing you to script repetitive tasks, create custom filters, and seamlessly incorporate Mitmproxy into your workflows. These capabilities make it an essential tool for thorough network debugging.
Getting Started with Mitmproxy Today
Ready to dive in? Installing Mitmproxy on macOS is straightforward with Homebrew:
brew install mitmproxy
Once installed, configure your browser to use http://localhost:8080 as its proxy, and install the CA certificate by navigating to http://mitm.it.
Try out different proxy modes to see what fits your workflow best. The regular mode is great for most tasks, but exploring options like local capture, WireGuard, or reverse proxy can unlock new possibilities.
As you get familiar with the basics, start leveraging Mitmproxy's scripting capabilities. Automate repetitive tasks or customize how traffic is handled using its Python API. The documentation provides a great starting point for building tailored solutions.
Whether you're debugging APIs, testing mobile apps, or conducting security audits, Mitmproxy can quickly become a cornerstone of your macOS development toolkit. Start with a single task and build your expertise as you go - the possibilities are endless.
FAQs
How does Mitmproxy work with HTTPS traffic without affecting app functionality?
Mitmproxy manages encrypted HTTPS traffic by functioning as a man-in-the-middle (MITM) proxy. Essentially, it steps into the communication chain between your application and the target server, enabling it to decrypt and examine the data being exchanged. To achieve this, Mitmproxy creates a temporary SSL certificate for each site and requires the client to trust its certificate authority (CA).
When you install Mitmproxy's CA certificate on your device, it can decrypt HTTPS traffic smoothly, without interfering with the normal operation of your applications. This makes it an invaluable tool for developers and testers who need to monitor, analyze, and debug network traffic while ensuring everything runs as expected.
What are the differences between Mitmproxy, Mitmweb, and Mitmdump?
Mitmproxy Interfaces: Tailored for Different Needs
Mitmproxy provides three interfaces, each designed to handle specific scenarios:
- Mitmproxy: This is a command-line tool with an interactive console, perfect for real-time inspection and modification of HTTP(S) traffic. It keeps all traffic flows in memory, making it a great choice for smaller debugging tasks.
- Mitmweb: If you prefer a visual approach, Mitmweb offers a browser-based interface that displays traffic in a graphical format. While it provides a user-friendly experience similar to Mitmproxy, it's still in beta and might not include some advanced features.
- Mitmdump: This is a non-interactive command-line tool focused on logging HTTP(S) traffic. Think of it as a simplified version of Mitmproxy, built for capturing data without the need for real-time interaction - perfect for automated workflows.
Whether you need a console for hands-on debugging, a GUI for easier navigation, or a lightweight tool for logging, Mitmproxy has you covered.
What should I consider to ensure security when using Mitmproxy to analyze network traffic?
When working with Mitmproxy to intercept and analyze network traffic, keeping security at the forefront is crucial to safeguard sensitive information and block unauthorized access.
- Certificate Management: Use Mitmproxy’s certificate authority (CA) with care. Ensure the client device trusts it properly, as mishandling the CA certificate could lead to security vulnerabilities.
- Handling Sensitive Data: Since intercepting HTTPS traffic can reveal private information, it's essential to use Mitmproxy responsibly to minimize the risk of exposing sensitive data.
- Secure Environment: Always operate Mitmproxy within a private, secure network. Avoid running it on public Wi-Fi, where the risk of unauthorized access is much higher.
These steps can help ensure a safer and more reliable experience when using Mitmproxy for debugging and traffic analysis.