
What is SSL pinning, and how does it work?
SSL pinning is a technique that secures the connection between an app and its server by ensuring the app only trusts specific certificates or public keys. This prevents hackers from intercepting or tampering with sensitive data, even during a Man-in-the-Middle (MITM) attack. Here's how it works:
- Certificate Pinning: Stores and verifies the entire server certificate.
- Public Key Pinning: Validates only the server's public key, offering more flexibility during certificate changes.
Key Benefits:
- Blocks unauthorized certificates.
- Protects against compromised Certificate Authorities.
- Ensures secure data transmission.
Quick Comparison:
| Feature | Certificate Pinning | Public Key Pinning |
|---|---|---|
| Ease of Implementation | Easier | Requires key extraction |
| Certificate Rotation | App updates needed | Works if the public key stays |
| Security | Secure | Slightly more secure |
| Maintenance | Higher overhead | Lower overhead |
SSL pinning is critical for apps handling sensitive data, such as financial or personal information. Choose between static or dynamic pinning based on your app's needs, and always plan for certificate updates to avoid disruptions.
SSL Pinning Technical Overview
Implementing SSL pinning requires selecting a method that balances security with ease of maintenance.
Choosing Between Certificate and Public Key Pinning
When it comes to SSL pinning, there are two main approaches: certificate pinning and public key pinning. Each has its own strengths and considerations.
- Certificate Pinning: This method involves storing the entire server certificate within your application and verifying it against the certificate presented during a connection attempt.
- Public Key Pinning: Instead of the full certificate, this approach validates only the server's public key extracted from the certificate.
Here's how the two methods compare:
| Feature | Certificate Pinning | Public Key Pinning |
|---|---|---|
| Ease of Implementation | Easier to implement | Requires extracting the public key |
| Impact of Certificate Rotation | App updates needed when certificates change | Works seamlessly if the public key remains unchanged |
| Security | Secure | Slightly more secure by focusing on the public key |
| Maintenance Overhead | Higher (due to frequent updates, especially with ~90-day certificates) | Lower (as long as the public key stays the same) |
The choice between the two often depends on your application's update process and how often certificates are rotated. Public key pinning is ideal for environments like IoT devices or embedded systems, where updates are infrequent. On the other hand, certificate pinning is a simpler option for apps that can handle regular updates.
Static and Dynamic Pin Management
SSL pins can be managed in two ways: statically or dynamically. Each approach comes with its own set of trade-offs.
- Static Pinning: Pins are hardcoded into the application. While this offers quick and reliable access, any certificate change requires an app update and redeployment.
- Dynamic Pinning: Pins are updated in real time, which provides several advantages:
- Security: Regular pin rotation reduces exposure to potential threats.
- Certificate Management: Removes the need to pre-configure all possible backend certificates.
- Maintenance: Allows seamless certificate updates without requiring app updates.
To ensure robust SSL pinning, it's critical to use established frameworks and thoroughly tested security configurations. Avoid building custom validation mechanisms from scratch, as these can introduce vulnerabilities.
macOS SSL Pinning Setup
Building on the basics of SSL pinning, this section dives into how to implement it in macOS applications using TrustKit. Proper configuration is key to ensuring secure communication without introducing unnecessary risks. Here’s how to set up TrustKit for your macOS app.
Setting Up Pins in macOS Apps
Integrating TrustKit into a macOS application involves a methodical process to balance robust security with minimizing potential issues.
- Generate SSL Pins: Use TrustKit's Python helper to create base64-encoded SHA-256 pins from your server's SPKI.
- Add TrustKit to Your Project: Incorporate TrustKit into your app using CocoaPods, Carthage, or Swift Package Manager.
-
Define Pinning Policy: Set up a configuration dictionary that outlines your pinning rules. Include key parameters like:
Configuration Key Purpose Recommended Setting kTSKEnforcePinningControls pin validation Begin with NOduring testingkTSKSwizzleNetworkDelegatesEnables auto-swizzling Use YESfor simpler appskTSKPinnedDomainsSpecifies domain configurations Include both primary and backup pins
"Public key pinning can be dangerous and requires more than just code-level changes in your App. If you make a mistake, you might cause your App to pin a set of keys that validates today but which stops validating a week or a year from now, if something changes. In that case, your App will no longer be able to connect to its servers and will most likely stop working, until it gets updated with a new set of pins." – TrustKit Documentation
Testing Tools for macOS
After configuring TrustKit, it’s essential to test your setup thoroughly. Use specialized tools and strategies to ensure everything works as intended.
Debug Configuration Setup
Create a separate debug configuration tailored for testing. Here are some common testing needs and their solutions:
| Testing Need | Solution | Implementation |
|---|---|---|
| Traffic Inspection | SSL Kill Switch 2 | Inject with LLDB |
| Development Testing | Disabled Pinning | Set kTSKEnforcePinning to NO |
| Certificate Testing | Self-signed CA | Use test certificates for development |
For development environments, temporarily disable pinning using LLDB or environment variables to facilitate testing.
Best Practices for Testing
- Use separate configurations for development and production, ensuring a dedicated pin-testing suite is in place.
- Sign your code during development to avoid injection vulnerabilities.
- Implement robust error handling to catch and diagnose pinning failures during testing.
"Unless you are confident that you understand the Web PKI that you can manage the App servers' cryptographic identity very well, you should not use key pinning." – TrustKit Documentation
ReqRes SSL Pinning Features
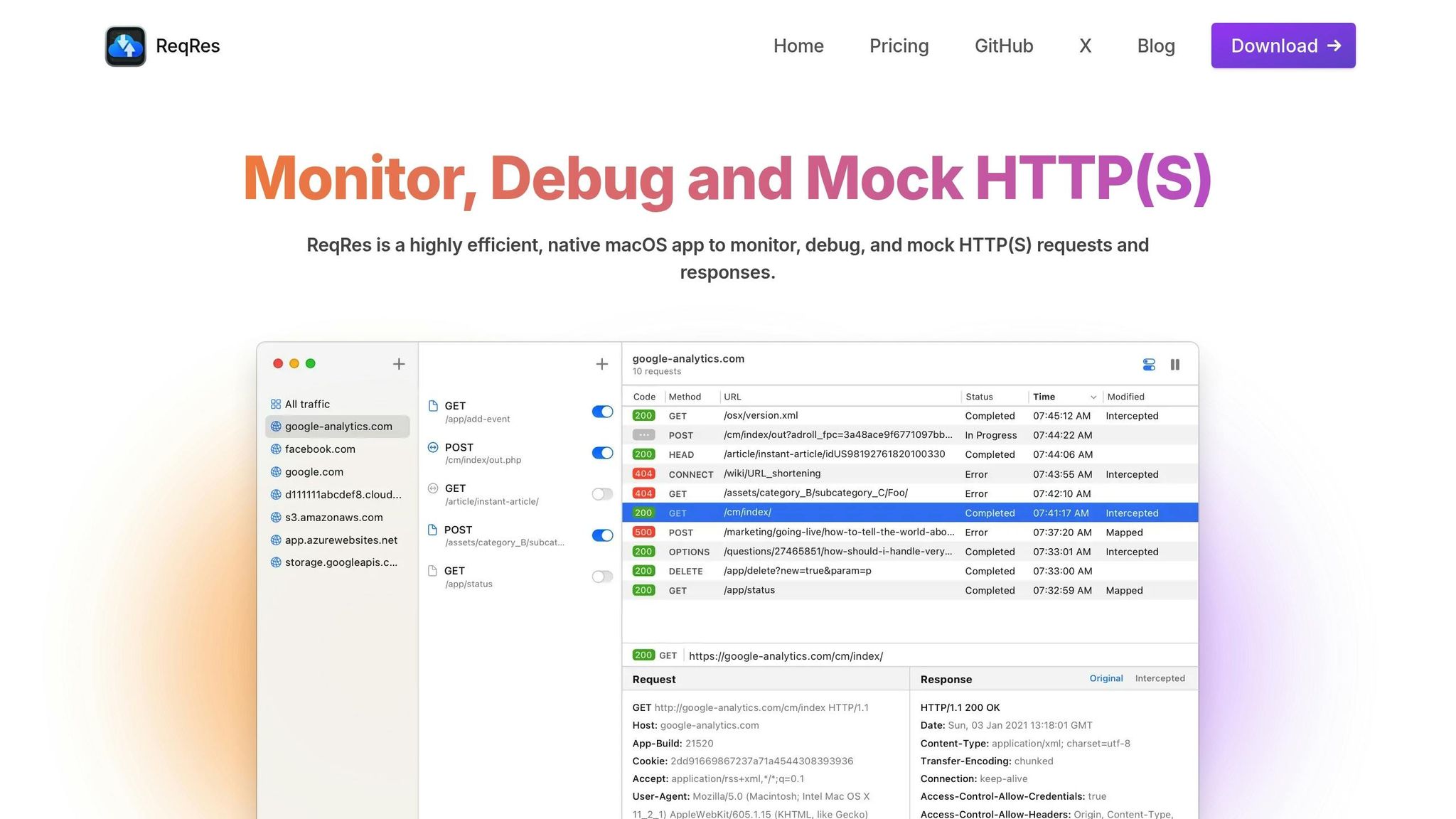
Expanding on its technical foundation and macOS setup, ReqRes takes security a step further by offering built-in SSL pinning capabilities and advanced traffic analysis tools. With seamless integration into macOS security frameworks, ReqRes ensures secure and real-time inspection of HTTP(S) traffic, making it a valuable tool for macOS developers.
Setting Up SSL Pinning in ReqRes
Configuring SSL pinning in ReqRes enhances security while allowing effective traffic monitoring. Here's a breakdown of the key elements involved:
| Configuration Element | Purpose | Implementation Details |
|---|---|---|
| Certificate Management | Validates SSL certificates | Import and validate certificates |
| Domain Configuration | Specifies target domains | Define domains for pinning |
| Security Level | Sets strictness levels | Adjust validation and enforcement |
| Backup Certificates | Provides failover options | Add alternative certificate pins |
ReqRes simplifies the process by maintaining separate configurations for development and production environments. This makes transitioning between testing and deployment smooth and efficient.
Steps to Implement Certificates
- Use the ReqRes certificate manager to import production SSL certificates.
- Identify and specify the domains that require certificate validation.
- Set up validation rules and adjust enforcement levels as needed.
Once configured, ReqRes empowers you to monitor and analyze HTTPS traffic effectively, all while maintaining strict security standards.
Analyzing Traffic with ReqRes
ReqRes goes beyond SSL pinning by offering a robust suite of tools for HTTPS traffic analysis. These features are particularly useful when working with secure applications, as highlighted in studies of Meta's Messenger app.
Key Traffic Analysis Features
The platform combines security validation with comprehensive monitoring tools:
| Feature | Function | Security Impact |
|---|---|---|
| Certificate Validation | Ensures certificates are authentic | Blocks unauthorized access |
| Error Logging | Tracks SSL handshake issues | Helps diagnose connection problems |
| Request Monitoring | Captures HTTPS traffic data | Maintains security during inspection |
Even with SSL pinning enabled, ReqRes simplifies the process of identifying and resolving common issues like "SSL Handshake Failed" errors. Its tight integration with macOS security features ensures smooth operation, enabling developers to quickly troubleshoot and address SSL-related challenges without compromising on security.
SSL Pinning Maintenance Guide
Keeping SSL pinning functional in production apps demands thoughtful planning and consistent management. This ensures your applications remain secure while avoiding service interruptions.
Certificate Updates and Renewal
Managing certificates effectively is key to maintaining uninterrupted service. Here's a helpful timeline to guide you through the process:
| Phase | Action | Timeline |
|---|---|---|
| Planning | Identify pinned certificates and their expiration dates | 90 days before expiration |
| Preparation | Generate new certificates and update the pin list | 60 days before expiration |
| Deployment | Release app updates with both old and new certificates | 30 days before expiration |
| Cleanup | Remove expired certificates from the pin list | After certificate expiration |
Two essential strategies to focus on:
- Certificate Transition Strategy: Always include multiple certificates in your pin list. This allows you to replace certificates smoothly without disrupting services.
- Public Key Management: Opt for public key pinning. If your new certificates share the same private key, you can avoid frequent app updates.
"SSL Pinning is a technique that we use in the client side to avoid man-in-the-middle attack by validating the server certificates again even after SSL handshaking." - Zhang QiChuan
Once your certificate strategy is updated, ensure you have a solid backup plan in place.
Backup Certificate Planning
A well-designed backup plan complements your SSL pinning setup, helping you maintain security while preventing service outages.
Primary Backup Mechanisms
| Backup Element | Purpose | Implementation |
|---|---|---|
| Intermediate Certificates | Provide fallback validation | Pin intermediate CA certificates |
| Public Key Redundancy | Maintain connection integrity | Use consistent key pairs across certificates |
| Emergency Response | Handle compromised certificates | Prepare rapid deployment procedures |
Key practices to enhance your backup strategy:
- Alternative Certificates: Always have alternative certificates ready for immediate deployment in case your primary certificate fails.
- Testing Configuration: Use tools like Charles Proxy to test your new setup and confirm that SSL pinning effectively blocks potential man-in-the-middle (MITM) attacks.
- Certificate Monitoring: Regularly monitor certificate expiration dates and integrity to avoid unexpected issues that could impact your app's functionality.
Summary
SSL pinning is a security measure that embeds trusted certificates or public keys directly into an app, providing a strong defense against man-in-the-middle (MITM) attacks. By ensuring that the app communicates exclusively with legitimate servers - even in the face of phishing attempts - it offers an added layer of protection beyond what standard HTTPS protocols provide. This technique not only strengthens app security but also complements the advanced strategies discussed earlier.
Here’s a quick breakdown of key implementation strategies:
| Strategy | Benefit | Best Practice |
|---|---|---|
| Public Key Pinning | Simplifies certificate management | Pin multiple keys, including backups |
| Certificate Pinning | Enforces strict certificate validation | Use overlapping certificate pairs |
| Backup Planning | Prevents potential service outages | Implement automated monitoring systems |
The success of SSL pinning largely depends on consistent upkeep and vigilance. Organizations need to routinely assess the strength of their cryptographic measures and stay alert to new security challenges. Regular updates and proactive monitoring, as previously highlighted, are critical for maintaining this level of protection.
FAQs
What are the risks of improperly implementing SSL pinning in an app?
Implementing SSL pinning the wrong way can backfire, leaving security vulnerabilities wide open. For instance, if the pinning setup is overly strict, apps might reject legitimate certificates after server updates, causing connection issues. On the flip side, a lax approach can make it easier for attackers to carry out Man-in-the-Middle (MitM) attacks, potentially exposing sensitive data.
To minimize these risks, it's crucial to stick to best practices. This includes managing certificate updates carefully and conducting thorough testing during development. Poor implementation not only weakens security but can also disrupt the user experience, so thoughtful planning is absolutely essential.
What is SSL pinning, and how does it make applications more secure?
SSL pinning is a security method designed to ensure that an application only accepts a specific server’s certificate or public key. This approach provides an added layer of defense against man-in-the-middle (MITM) attacks, where an attacker might intercept or alter data exchanged between the app and its server.
Unlike standard HTTPS, which relies on a certificate authority (CA) to establish trust, SSL pinning takes things a step further. It embeds the server's certificate or public key directly into the app's code. As a result, even if a CA is compromised or a fake certificate is issued, the app will reject it unless it matches the pinned certificate. This technique makes it much harder for attackers to exploit vulnerabilities and helps secure sensitive data and API communications within your applications.
What’s the difference between static and dynamic SSL pinning?
When it comes to SSL pinning, there are two main approaches: static and dynamic.
Static SSL pinning involves hardcoding a server's certificate or public key directly into the app’s code. This ensures the app will only trust that specific certificate or key. While this method is highly secure, it comes with a drawback - any updates to the certificate require releasing a new version of the app, which can be cumbersome.
Dynamic SSL pinning, on the other hand, allows the app to fetch and validate certificates or public keys during runtime. This makes it easier to handle changes, like certificate updates, without needing to push a new app version. However, this flexibility requires additional measures to ensure the process remains secure.
Both approaches have their strengths and limitations, and the best choice depends on your app’s security requirements and how often updates are needed.